Before we talk about Juniper (and Mist, specifically), let me take you way back in time to another acquisition.

I wrote that article back in 2012 after several great years of enjoying Meraki as a pioneering cloud-managed network vendor at the same time I was dealing with endless bugs in Cisco’s wireless controllers and APs. The cultures of the two companies seemed so different- Cisco tends to be cavalier (in my opinion) about bugs especially in their WLAN related code sets, and customers are very much an extension of the QA process whether they want to be or not. Code roulette is a fact of life, and disruptive frequent remedial code upgrades and engineering builds were a fact of life back then. By contrast, Meraki generally worked well, and when trouble rarely hit, support was extremely responsive.
Since the acquisition, Cisco gave Meraki an extremely long leash to seemingly operate mostly independently (at least from the customer perspective). They are only just now getting around to consolidating business units, switches and access points and pushing even legacy management towards the cloud dashboard. It needs to be noted that the Cisco Catalyst/Aironet and Meraki lines and customer bases were far enough apart in function and philosophy that there was room for both to remain generally unsullied by each other for more than a decade.
Now on to HPE purchasing Juniper.
Unlike the Cisco/Meraki experiment that let customers on both sides breathe easy for so many years, it’s not gonna be that warm and fuzzy with this one. For me, HPE and Juniper more specifically equals Aruba and Mist- and that facet of this acquisition makes me uncomfortable. I have no idea how it’s going to turn out where the rubber meets the road- but I do know that as a Mist customer I did not choose Aruba as a vendor (nor did Aruba customers choose Mist and I respect that). Everyday, customers are choosing Aruba versus Mist and visa versa for their own reasons and requirements.
It’s highly likely that either Mist or Aruba will dominate at the end of the sausage making and there will be pain for many of us on the leftover pile. For anyone to have a vendor you didn’t choose forced down your throat is not a tasty thought regardless of which side of this you are on as a current customer. We all have no choice but to wait this out, but from the customer side let me share some of what sucks in the meantime.
We the customers were never asked.
I’m getting a bit fried on seeing one talking head after another pontificating about how this acquisition somehow creates “greater choice” for customers. That implies we want “greater choice” which will actually be LESS choice in the end. Just shut up already on that- we’re not that stupid out here in networking wilds. We selected what we selected after RFPs and product trials and “greater choice” in the future is just empty BS in this discussion. A clever marketing phrase brings no comfort while we all wait to see how badly our cheese will both be genetically altered AND moved once it all plays out. Don’t believe me, Mist and Aruba execs? Survey your customers. Other than internal evangelists (and zealots) who are thumping their chests about which company is better and will “win” in the end, there aren’t a lot of people that I’ve spoken to that are particularly energized about this whole thing.
Vendor messaging only adds to the tension.
In typical vapid marketing bullshitspeak, HPE promises “accelerated value” from the acquisition. Juniper makes it sound like their AI was the sexy milkshake that brought HPE to the Juniper yard. Some headlines out there seem to push the point.

But then there’s that Aruba evangelist who frequently posts on X taking potshots at everyone else’s AI while touting Aruba’s own, and has only stepped up his salvos since the purchase was announced.

The “mic drop” is from Neri implying that Aruba Central will subsume Mist’s AI and that somehow Aruba Central’s customer numbers prove it’s the right thing to do (?) Yet in other announcements the Mist exec team will supposedly lead the integrated business unit when all the dust settles- so Juniper’s AI must be better (?) AI, AI. AI… blah blah friggin blah. So did HPE buy Juniper because it has better AI despite the passions of their own insiders? On that topic, I need to say something…
Newsflash: AI is a building block and not THE PRODUCT in network access systems. I’m here to tell you that a vendor’s glossy can spin AI to be the grand solve-all, yet their code can be endlessly problematic, and their reporting and support UIs- you know, the daily important stuff to keeping networks running- can still suck ass. I’m talking about no specific vendor here and multiple vendors at the same time. Babies are being thrown out with the bathwater and customers are suffering from AI overhype while the important but unsexy basics of usability and stability aren’t being prioritized in spots.
Speaking of posts on X- Sam the Man Clements hit this whole mess right on the head here:
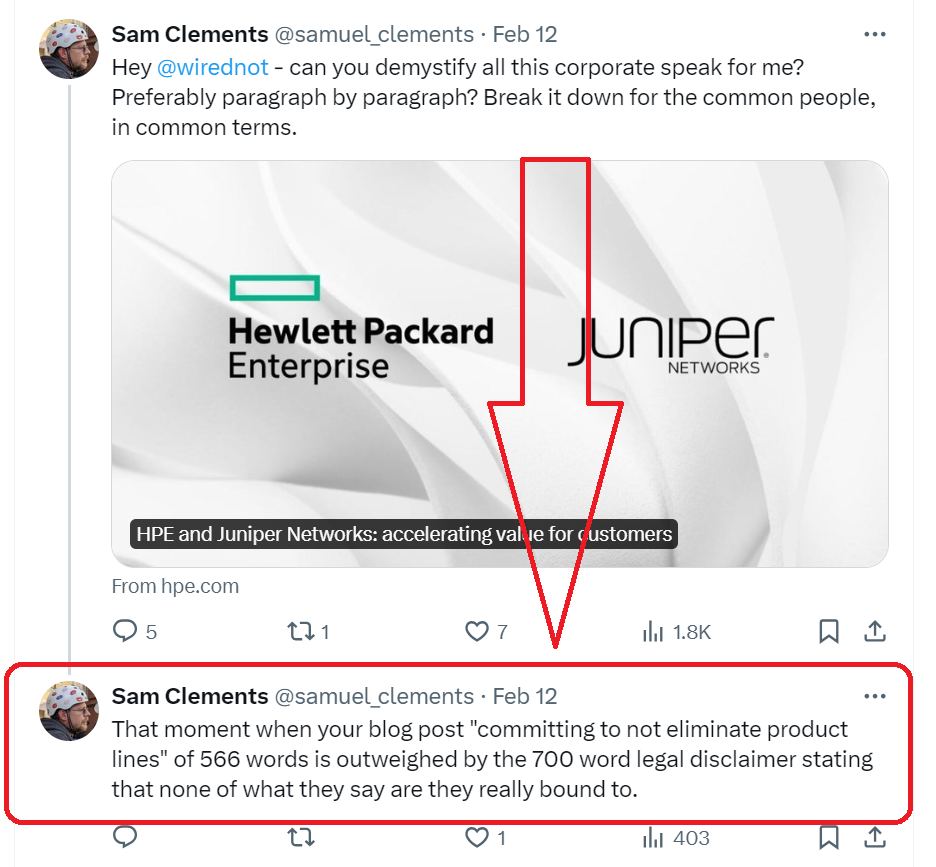
Nothing is gonna change- we promise! But it’s not a promise you can can count on…
Then there’s the general industry covering media…
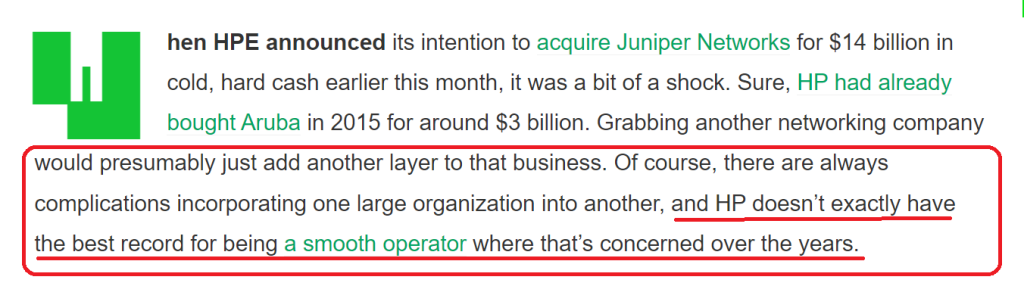
And the pundits…

The rest of the year is gonna suck.
It wouldn’t break my heart if this acquisition is blocked, but I doubt it will be. Which means customers on both sides of the deal get to just wait and see what is to come of it all. Small environments that don’t like the results can fairly easily jump ship and go to Cisco, Extreme, Fortinet, or whoever else is out there as alternatives. Large customers (outside of the government who gets to spend everyone else’s money) don’t have the luxury of simply scrapping thousands of access points (modern APs list for over $2K apiece these days, but that insanity is fodder for another blog) and the rest of their access environments, and so many will absolutely have to take whatever’s coming whether they like it or not. That in itself creates enough anxiety- but piled on top we now get to spend the rest of 2024 hearing meaningless promises of accelerated value and tit-for tat proclamations of which vendor is “better”, along with the business-side analysis that spins the pending deal as wonderful or terrible depending on who is pushing the message.
Fun times.
Not.