If you manage a network today, you are likely getting peppered by the drumbeat of ideas for new ways of doing networking. Concepts like SDN, automation, AI, machine learning and fabric are becoming the next-generation lexicon of connectivity. Sure, us long-timers have heard it all before in different incarnations- but this is a pot that is really beginning to simmer while the industry tries to collectively move the way enterprise networks are done forward.
Meanwhile, those of us in the trenches have production environments to run. It’s not particularly comfortable to contemplate moving our own cheese in response to abstract promises of better ways and sunnier days, but Extreme Networks,Inc. may just be the company to break down the wall of hype and deliver the industry to the actual realization of the promise of network fabric architectures.
Before I get into why I think Extreme is the most likely company to show that the new network magic can actually be delivered in a way that leads to wide-scale adoption, let me share one of the best whitepapers I’ve read yet on what vendors are actually trying to do with the latest fabric initiatives. All the expected promises of simplification and reduced OpEx are in the Extreme Automated Campus document, but so is an excellent summation on some of the not-so-obvious advantages and evolutions that come with a properly implemented automated network. Among them:
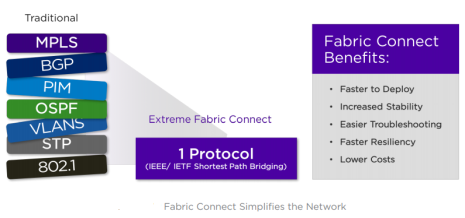
- The use of 802.1aq Shortest Path Bridging (SPB) as essentially a single-protocol replacement for traditional building blocks like MPLS, BGP, multicast PIM, OSPF, VLANs, and others. That’s huge, and reduces complexity by several orders of magnitude in large environments.
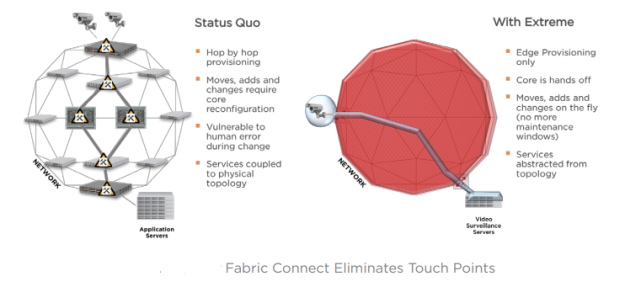
- The notion that hop-by-hop network provisioning is a thing of the past. The network core is essentially unseen to most network admins, and all changes are done on the edge (live and without outages/maintenance windows).
- User and device policies are the basis for automated network changes, and constant analytics provide feedback used to tune performance and anticipate issues.
- By employing hyper-segmentation, a security breach in one part of the network is contained like never before, as the rest of the network is invisible to the bad guys because the old protocols leveraged for nefarious purposes are no longer present.
- The use of APIs mean that third-party network components can interoperate with Extreme’s Automated Campus.
There’s a lot more to the whitepaper, and I encourage anyone who’s been underwhelmed by other explanations of what network fabrics/automation are supposed to deliver read it as an excellent primer.
As I digested insights from Extreme’s whitepaper, I also found myself reminded that obsolescence can be insidious with the legacy methods we do networking with now. Dated designs can underperform today and fail tomorrow while we miss subtle signs of trouble because of disparate logs and dashboards. This isn’t news to anyone running large business networks, and is why automated analytics has a fairly strong appeal. This brings me back to Extreme and what puts them at the head of the pack within the networking space.
Extreme pioneered and set the bar high for network analytics with its ExtremeAnalytics platform. The value proposition has been proven in many cases, via a range of customer relationships. Where other networking companies are relying on third -parties or are just getting around to developing analytics solutions, Extreme has been optimizing networks based on machine-learning analytics for years.
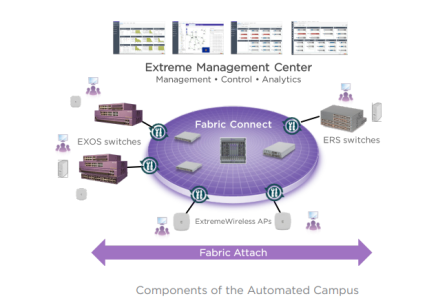
Then there is Extreme’s purchase of Avaya earlier this year. By my estimation, Avaya was the absolute creator of SDN-enabled network fabric environments. I visited the company’s Silicon Valley facilities in 2014 during Tech Field Day, and got a first-hand look at the impressive technology that has become part of Extreme’s fabric offerings. Extreme now has real-world fabric customers and a mature offering among newcomers to the game.
The fabric/SDN thing is here to stay as evidenced by the market leaders all talking it up as “what comes next” in unified networking. But how to get there – and whether you want to stay with your incumbent networking vendor for the leap – is a more complicated discussion. Some of the new initiatives feel cobbled-together, i.e. placing frameworks of APIs into legacy hardware that may not have the best track-records for reliability. I’m of the opinion that some vendors are trying to figure out how to proceed with network-wide fabric methods, while painting beta-grade efforts up with glitz and catchy slogans (though lacking depth and a track-record). This just isn’t the case for Extreme.
Extreme has done a great job in integrating their acquired Avaya fabric assets with their established portfolio and consolidating it all (along with their excellent technical support) into the Extreme Automated Campus. It’s new, on paper, but made up of mature industry-leading building-blocks. This is why I see Extreme as the one to beat in this space.
Learn more about the Automated Campus solution here.
Register for Extreme’s upcoming Automated Campus webinar here.
FTC-required disclosure: I was compensated to comment on the Extreme Networks Automated Campus referenced in this blog, by PR company Racepoint Global. I have no direct business relationship with Extreme Networks, and in no way claim to be an Extreme Networks customer or representative of Extreme Networks. The opinions expressed here are my own, and absolutely true at the time of publication.



